Ransomware attacks have become one of the most common and costly cyber threats facing businesses today. From encrypting your files to shutting down your systems, ransomware can bring your operations to a standstill in seconds. And even if the damage is contained quickly, the disruption, recovery work, and reputational impact can be significant.
That’s why ransomware and cyber extortion coverage is one of the most essential components of a modern cyber insurance policy. At Redwood Insurance Solutions, we help Michigan businesses understand how this coverage works — and why it's critical protection in today's threat landscape.
What Is Ransomware and Cyber Extortion Coverage?
Ransomware and cyber extortion coverage helps protect your business financially when criminals:
-
Demand a ransom payment to restore access to your systems or data
-
Engage in double extortion by encrypting your files and stealing (exfiltrating) sensitive data, then threatening to leak or sell it
-
Disrupt your operations through encryption or network lockdown
-
Use intimidation tactics to pressure your company into paying
This coverage helps you manage the incident, recover your systems, and minimize business interruption while experts negotiate and resolve the threat.
What Cyber Insurance Typically Covers During a Ransomware Attack
While policies vary, ransomware and cyber extortion coverage usually includes support in these key areas:
1. Ransom Payments (When Legal and Approved)
If a ransom is legally payable and your business chooses to pay it, many cyber policies cover the actual ransom amount. This process is heavily regulated: insurers cannot pay extortion demands to individuals or groups on U.S. OFAC sanction lists, and all payments require legal review before approval.
Coverage may also include:
-
Cryptocurrency acquisition costs
-
Broker or transaction fees required to facilitate the payment
2. Cybersecurity and Negotiation Experts
One of the most valuable elements of coverage is immediate access to specialized professionals, such as:
-
Cyber extortion negotiators
-
Digital forensic investigators
-
IT recovery specialists
-
Legal and regulatory counsel
-
Crisis management and PR experts
These experts are often the difference between a fast recovery and a prolonged operational shutdown.
3. System Restoration and Data Recovery
Once the immediate threat is contained, your cyber policy can help pay for:
-
Restoring encrypted or corrupted data
-
Rebuilding systems and applications
-
Testing and safely bringing systems back online
-
Implementing immediate, necessary security improvements directly related to the incident
Important: Most policies cover incident-specific recovery, not long-term security upgrades or modernization projects.
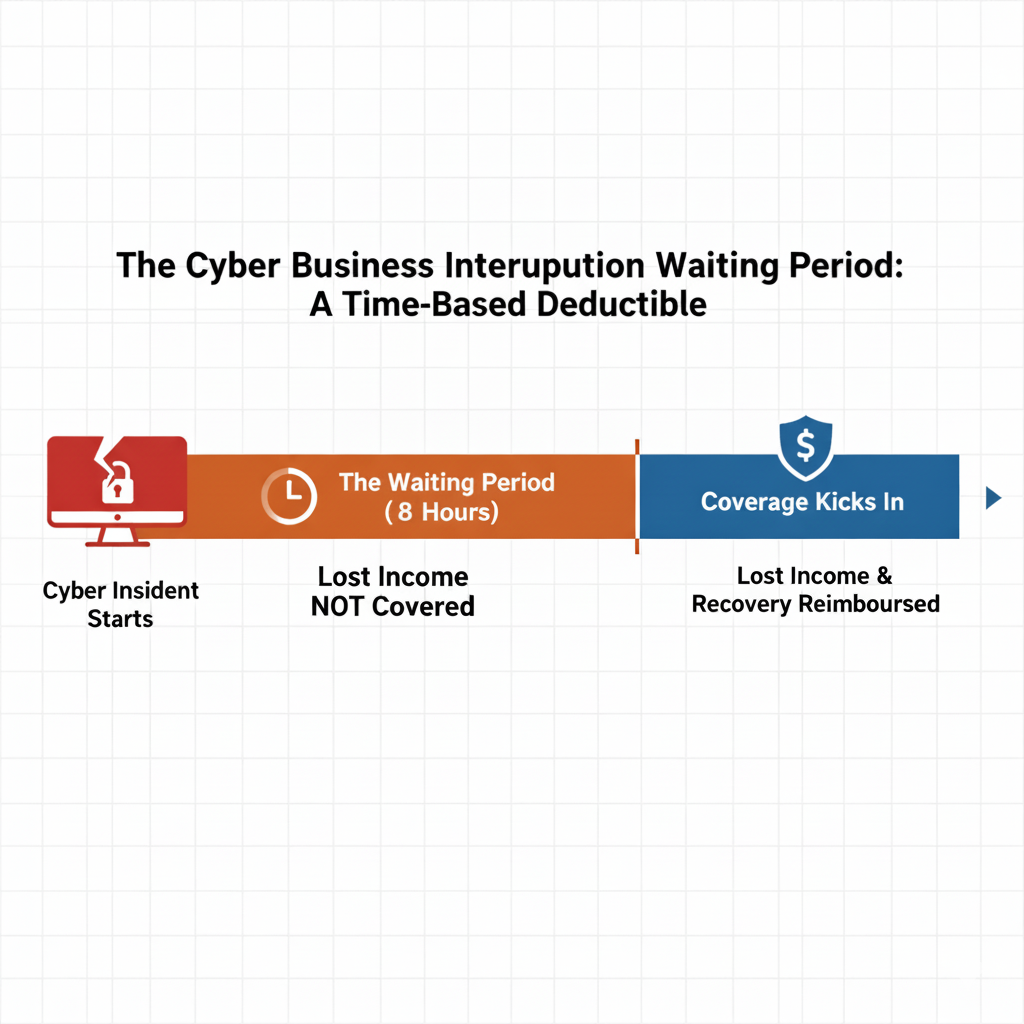
4. Business Interruption Losses
If ransomware takes your systems offline, your business may lose income during the outage. Cyber insurance can help reimburse:
-
Lost revenue
-
Extra expenses needed to keep operations running
-
Costs associated with delayed or disrupted services
This is essential for companies where even a few hours of downtime can be costly.
5. Extortion Threat Mitigation
If attackers threaten to leak stolen data unless you pay, cyber policies often cover:
-
Incident response guidance
-
Forensic containment
-
PR and crisis communication support
-
Credit monitoring or identity protection for impacted individuals
Why Ransomware Coverage Is So Important Today
Ransomware isn't just a threat to large corporations. Attackers increasingly target small and mid-sized businesses because they often lack advanced cybersecurity defenses.
Here’s why ransomware and cyber extortion coverage is essential:
-
Ransomware attacks continue to rise each year
-
Double extortion tactics are now standard practice
-
Downtime is expensive even if no ransom is paid
-
Recovery requires technical, legal, and operational expertise
-
Negotiation without experts can lead to costly errors
Cyber insurance delivers both financial protection and the expert support necessary to navigate these high-pressure situations.
Important Note on Policy Requirements
Modern cyber insurers increasingly require businesses to maintain specific baseline security controls, such as:
-
Multi-Factor Authentication (MFA) on email and all remote access
-
Regular, tested backups, stored offline or immutable
-
Endpoint protection and active monitoring
-
Employee security training
Failure to maintain these controls could jeopardize eligibility for coverage or affect claims.
The Bottom Line
Ransomware and cyber extortion threats aren't going away — but with the right cyber insurance policy in place, your business can respond quickly, restore operations, and minimize long-term damage.
At Redwood Insurance Solutions, we help Michigan businesses build strong cyber protection that includes ransomware coverage, business interruption support, system restoration, and ongoing risk-management guidance.
If you're unsure how your policy would respond to a ransomware attack, our team can walk you through the details — before you ever have to face one.